Data privacy compliance as code
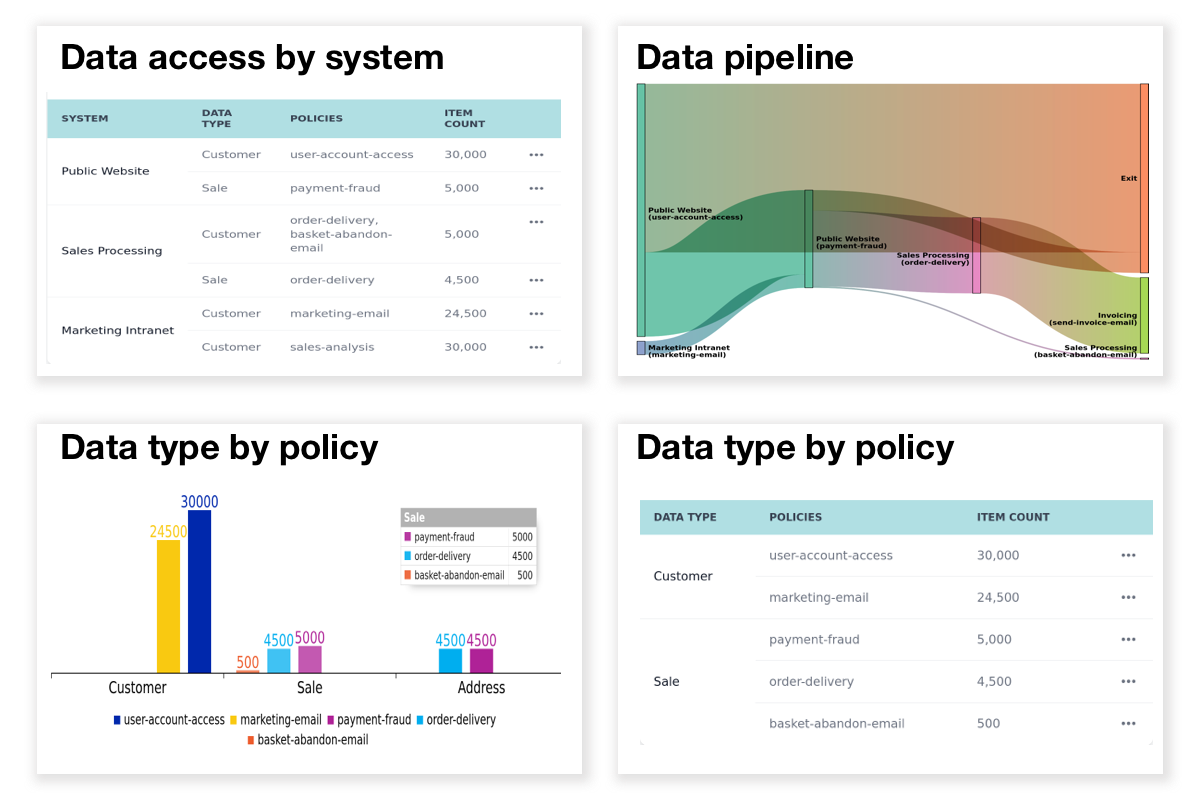
Personally identifiable information (PII) like names, telephone numbers and addresses remain your existing data stores, we never see it. As your code uses PII, it sends telemetry to PDS Metronome saying which identifiers were used and what the purpose was. If your code does not routinely delete sensitive data after it has served its stated purpose, it's very likely violating data privacy law. We help coordinate what data your many systems use and inform you when each identifier must be deleted to remain compliant (GDPR/CPRA/PIPEDA etc.) We provide automated risk reporting to understand reasons for data access, coordinate incident response, conduct impact assessments, and help you confidently expire data that is no longer used.